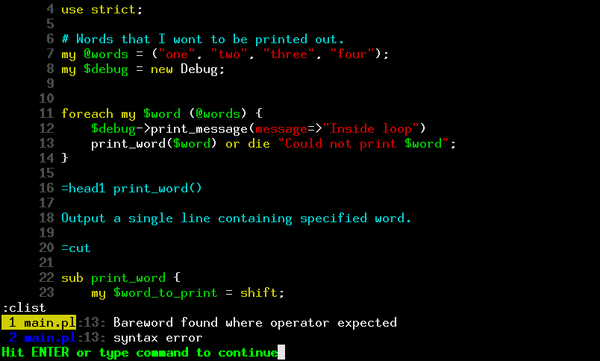
Script PHP com intuito de testar varias URL ao mesmo tempo, simulando uma requisição http Método GET.
Definindo o Arquivo TXT que contem as URL por padrão devem sem uma embaixo da outra
Ex:
http://site01.com.br/index.php?id=
http://site02.com.br/index.php?main=
http://site03.com.br/index.php?ok=
...Assim por diante.
Seu script de Teste pode ser um pbot enfim fica da sua escolha.
Existe um script Testing RFI Send envia sites vulneráveis para seu e-mails
Script teste: http://pastebin.com/krZi3W8E
GoogleINURL - Brasil pesquisa avançada.
Grupo voltado a busca detalhada no motor de pesquisa google. Utilizando operadores especiais google O que é Google hacking?
É uma pirataria de informática técnica que utiliza o
Google Search e outras Google aplicativos para encontrar falhas de segurança
na configuração e código de computador.
SCRIPT PARA ESTUDOS.
By GoogleINURL
blog.inurl.com.br